Navigation
Install the app
How to install the app on iOS
Follow along with the video below to see how to install our site as a web app on your home screen.
Note: This feature may not be available in some browsers.
More options
-
Welcome, guest!
Why not take a moment to register an account?
If you already have an account, remember to Log In!
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
HSE/Department of Health Hack (1 Viewer)
- Thread starter pete
- Start date
- Replies 112
- Views 6K
- Watchers 1
- Thread starter
- #2
“effected” ffs.
- Thread starter
- #3

Bitcoin ransom will not be paid following cyber attack on HSE computer systems
Taoiseach insists vaccination programme continues uninterrupted despite serious cybercrime incident
i'd say it's headless chicken centre in there this morning. i know a few lads who got jobs in the HSE and they talk in hushed tones about how dated a lot of the systems are.
You'd want to be some cunt all the same to attack a state healthcare system during a pandemic
This reminded me that Leo was in my dreams last night, sitting at our kitchen table. Seemed sound enough, maybe I'll vote FG next time*A possible eh, Taoiseach at the pub, this evening.
*joke
significant and sophisticated. Really. I've been working very much in the realm of IT security for the past few years. Most attacks of this nature are caused by some hacker (usually a spotty 16-year old who masturbates too much) exploiting carelessness. Who was it this year that said they were hacked by a very sophisticated network of hackers - when it turned out they put their fucking Kibana on the internet, unauthenticated.
Bitcoin ransom will not be paid following cyber attack on HSE computer systems
Taoiseach insists vaccination programme continues uninterrupted despite serious cybercrime incidentwww.irishtimes.com
Also, the HSE will have their IT systems managed by one of those massive consultancy companies (I can guess which one - I interviewed for them once and it was a mutual 'nah'), who stand up massive, overpriced projects to manage IT infrastructure for govt bodies, because no one knows any better to be able to tell them to cop on.
Then there was the Equifax 'hack' which was a huge scandal, it turned out they hadn't enabled 2fa and were issuing passwords like 'password' and weren't forcing people to change them.
The majority of hacks are carried out with 'trusted' credentials. Its not someone checking every combination of numbers and letters until they strike gold. Its either a weak password without 2FA, or the hackers have managed to get creds from a disgruntled ex-employee and use those.
Basically, someone generally opens the door to let them in.
From reading between the lines it sounds like someone got onto the systems and started replacing binaries and tools with their own version (rootkit, I think they call that), but even if they were in, was there no Intrusion Detection system in place? Even an opensource tool like OSSEC could have stopped this.
I scanned the register this morning to see if they were carrying the story, as they normally get into that level of detail. Nothing yet.
Maybe it is sophisticated. My guess is that it isn't.
- Thread starter
- #8
That’s the thing - the lads running these scams just need to get lucky once with getting the right person to click the right link. Eventually, someone will. I mean take look around any office and you can probably pick the likely candidates, but you’d be surprised the kind of people that fall for these things and then it’s GAME OVER MAN.significant and sophisticated. Really. I've been working very much in the realm of IT security for the past few years. Most attacks of this nature are caused by some hacker (usually a spotty 16-year old who masturbates too much) exploiting carelessness. Who was it this year that said they were hacked by a very sophisticated network of hackers - when it turned out they put their fucking Kibana on the internet, unauthenticated.
Also, the HSE will have their IT systems managed by one of those massive consultancy companies (I can guess which one - I interviewed for them once and it was a mutual 'nah'), who stand up massive, overpriced projects to manage IT infrastructure for govt bodies, because no one knows any better to be able to tell them to cop on.
Then there was the Equifax 'hack' which was a huge scandal, it turned out they hadn't enabled 2fa and were issuing passwords like 'password' and weren't forcing people to change them.
The majority of hacks are carried out with 'trusted' credentials. Its not someone checking every combination of numbers and letters until they strike gold. Its either a weak password without 2FA, or the hackers have managed to get creds from a disgruntled ex-employee and use those.
Basically, someone generally opens the door to let them in.
From reading between the lines it sounds like someone got onto the systems and started replacing binaries and tools with their own version (rootkit, I think they call that), but even if they were in, was there no Intrusion Detection system in place? Even an opensource tool like OSSEC could have stopped this.
I scanned the register this morning to see if they were carrying the story, as they normally get into that level of detail. Nothing yet.
Maybe it is sophisticated. My guess is that it isn't.
There’s also been a ton of exploits released lately on VPN appliances, and more recently Outlook Web Access….
- Thread starter
- #10
OkDon't take my webmail nerds.
- Joined
- Mar 21, 2004
- Messages
- 18,958
- Solutions
- 1
- Location
- in my head
- Website
- strikeaction.bandcamp.com
i'd say it's headless chicken centre in there this morning. i know a few lads who got jobs in the HSE and they talk in hushed tones about how dated a lot of the systems are.
my missus works in the head office. I have also heard similar things
Cormcolash
Well-Known Member
The HSE hack is clearly from Mossad after Leo had a go at Israel yesterday
i did see a comment saying 'israel wouldn't be so petty to go after hospitals would they?'
dunno if it was innocent or knowing.
dunno if it was innocent or knowing.
i had a meeting with broadcom/symantec during the week, about other issues, and they specifically warned us about conti.significant and sophisticated. Really. I've been working very much in the realm of IT security for the past few years. Most attacks of this nature are caused by some hacker (usually a spotty 16-year old who masturbates too much) exploiting carelessness. Who was it this year that said they were hacked by a very sophisticated network of hackers - when it turned out they put their fucking Kibana on the internet, unauthenticated.
- Thread starter
- #15
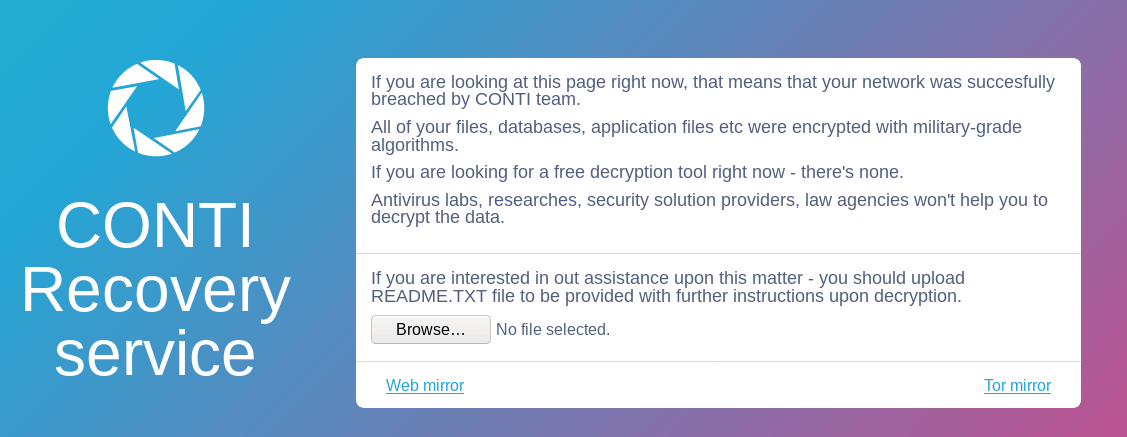
Conti Ransomware
In April, we saw the threat actors go from an initial IcedID infection to deploying Conti ransomware domain wide in two days and 11 hours. The threat actors stayed dormant for most of this time, before jumping into action on an early Saturday morning. The hands on keyboard activity lasted for...
 thedfirreport.com
thedfirreport.com
Caveman nuke is going to ask a few questions (bear in mind I think we are too reliant on technology and in many instances got by without it for generations)
Did any appointments happen today and if so what ?
A lot of consultations don't require internet or tech.
How much is the pandemic a factor in appointments being cancelled?
Is it simply the case that the HSE is so dependent on IT that the whole thing is permanently at risk of paralysis if hackers attack and there's no proper Plan B?
Feel free to call me a twit for asking this.
Did any appointments happen today and if so what ?
A lot of consultations don't require internet or tech.
How much is the pandemic a factor in appointments being cancelled?
Is it simply the case that the HSE is so dependent on IT that the whole thing is permanently at risk of paralysis if hackers attack and there's no proper Plan B?
Feel free to call me a twit for asking this.
OK - Paul Reid was just on TV so he said outpatient appointments were continuing as normal...
Is it simply the case that the HSE is so dependent on IT that the whole thing is permanently at risk of paralysis if hackers attack and there's no proper Plan B?
I've seen one of these attacks up close - the ransom is time as much as money - they might have a whole backup and just need to block the thing from coming again, or they might have no backup and be having huge arguments about things.
OK I get it.
Big time crisis, needs to be dealt with immediately.
If I was at a white House press conference I would ask - what's the point of nukes, NATO ? etc cause no one does.
Would be a laugh to hear what they would come out with
Big time crisis, needs to be dealt with immediately.
If I was at a white House press conference I would ask - what's the point of nukes, NATO ? etc cause no one does.
Would be a laugh to hear what they would come out with
The one I saw was crawling files on the HDs turning them into unworkable files and the network had to be physically disconnected to stop it. the bribe is the code to make them workable again, but generally it is an awful idea to give them money because then there is fuck all to stop them doing it again tomorrow. So best case everything was on a cloud somewhere and they got a stop to it and get the security in place and get back to normal, worst case half the Irish health database is corrupt and has to be bought back.
So I suspect that the techs communicating this quandry to the non techs might be where the sparks might fly.
So I suspect that the techs communicating this quandry to the non techs might be where the sparks might fly.
Users who are viewing this thread
Total: 1 (members: 0, guests: 1)
Activity
So far there's no one here
Similar threads
- Replies
- 0
- Views
- 318
- Replies
- 3
- Views
- 873
- Replies
- 1
- Views
- 746
Support thumped.com
Support thumped.com and upgrade your account
Upgrade your account now to disable all ads...
Upgrade now