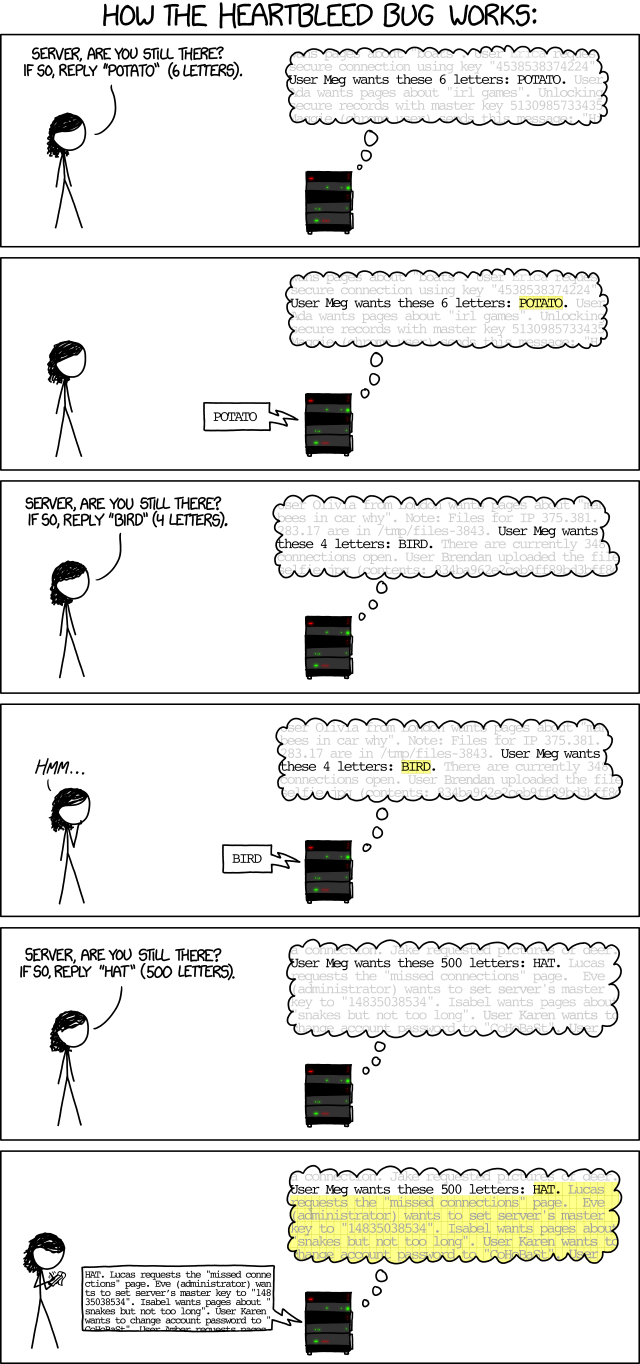
Should we be worried?
BBC News - Heartbleed bug creates confusion on internet
Computers vulnerable to the Heartbleed bug are actively being targeted online, say security experts.
However, it is not yet clear whether the scanning efforts are benign or are the work of cyber-thieves keen to steal data, they say.
The news comes as some security professionals and developers advised people to change all their passwords.
But Google said that logins for its services did not need to be reset unless they were used on other sites.
That contradicted advice from Yahoo's blogging platform Tumblr and the developers of the app If This Then That who have told users they should change their passwords "everywhere".
The conflicting guidance is further complicated by the fact that experts say updating a password is useless unless a site has patched its servers - but it is not always obvious to the public when this is the case.
Attack pattern
News about the Heartbleed bug broke on 8 April and has kicked off a frenzy of activity as web companies check to see if their systems are vulnerable.
The bug emerged in software that should have kept data passing between sites and users safe from scrutiny. Instead the bug meant that attackers could use specially crafted queries to slowly steal data from servers.
Ars Technica reported that some sites had seen evidence that networks of bots were probing them for the Heartbleed weakness long before the bug was publicised.
Information about scans of vulnerable servers are also circulating among security researchers. One scan turned out to pose no threat as whoever was behind it simply told the gaming company who ran the computers that they were leaking data.
"It's difficult to detect an attack unless you are actively looking for it," said Ken Munro, an analyst at security company Pen Test Partners. He added that many intrusion detection systems had now added signatures that spot the subtle signs that a Heartbleed-inspired attack is under way.
In addition, organisations running "honeypots" that try to trick hackers into attacking bogus web servers have written code that generates nonsensical server data in response to Heartbleed requests.
About 500,000 servers are vulnerable to the Heartbleed bug, statistics from net monitoring company Netcraft suggest.
Many large sites that ran vulnerable servers have now patched their systems and many others are following suit. However, a huge number of sites still remain vulnerable. Websites have sprung up that let people check if a site they use is vulnerable.
Conflicting advice has been given to web users from different companies about about whether they should be updating their passwords. Google said users did not need to change credentials; Facebook advised users to make a change; and others, such as web service If This Then That, said users should change all passwords.
Users should first check to see if a site they were using was vulnerable to the bug and whether they had taken action to fix it, said James Lyne, global head of research at Sophos. Changing a password on an unprotected site could still leave people open to data theft, he said.
In addition, he added, the rush to change passwords was likely to encourage phishing gangs to start sending out bogus messages advising people to reset or change their passwords.
"This is not the first defect of its kind and it certainly won't be the last, but it is one of the more serious faults we've seen in recent internet history," said Mr Lyne.
BBC News - Heartbleed bug creates confusion on internet
Computers vulnerable to the Heartbleed bug are actively being targeted online, say security experts.
However, it is not yet clear whether the scanning efforts are benign or are the work of cyber-thieves keen to steal data, they say.
The news comes as some security professionals and developers advised people to change all their passwords.
But Google said that logins for its services did not need to be reset unless they were used on other sites.
That contradicted advice from Yahoo's blogging platform Tumblr and the developers of the app If This Then That who have told users they should change their passwords "everywhere".
The conflicting guidance is further complicated by the fact that experts say updating a password is useless unless a site has patched its servers - but it is not always obvious to the public when this is the case.
Attack pattern
News about the Heartbleed bug broke on 8 April and has kicked off a frenzy of activity as web companies check to see if their systems are vulnerable.
The bug emerged in software that should have kept data passing between sites and users safe from scrutiny. Instead the bug meant that attackers could use specially crafted queries to slowly steal data from servers.
Ars Technica reported that some sites had seen evidence that networks of bots were probing them for the Heartbleed weakness long before the bug was publicised.
Information about scans of vulnerable servers are also circulating among security researchers. One scan turned out to pose no threat as whoever was behind it simply told the gaming company who ran the computers that they were leaking data.
"It's difficult to detect an attack unless you are actively looking for it," said Ken Munro, an analyst at security company Pen Test Partners. He added that many intrusion detection systems had now added signatures that spot the subtle signs that a Heartbleed-inspired attack is under way.
In addition, organisations running "honeypots" that try to trick hackers into attacking bogus web servers have written code that generates nonsensical server data in response to Heartbleed requests.
About 500,000 servers are vulnerable to the Heartbleed bug, statistics from net monitoring company Netcraft suggest.
Many large sites that ran vulnerable servers have now patched their systems and many others are following suit. However, a huge number of sites still remain vulnerable. Websites have sprung up that let people check if a site they use is vulnerable.
Conflicting advice has been given to web users from different companies about about whether they should be updating their passwords. Google said users did not need to change credentials; Facebook advised users to make a change; and others, such as web service If This Then That, said users should change all passwords.
Users should first check to see if a site they were using was vulnerable to the bug and whether they had taken action to fix it, said James Lyne, global head of research at Sophos. Changing a password on an unprotected site could still leave people open to data theft, he said.
In addition, he added, the rush to change passwords was likely to encourage phishing gangs to start sending out bogus messages advising people to reset or change their passwords.
"This is not the first defect of its kind and it certainly won't be the last, but it is one of the more serious faults we've seen in recent internet history," said Mr Lyne.